Operation Jacana is a targeted cyberespionage campaign against a Guyanese governmental entity, likely by a Chinese threat group.
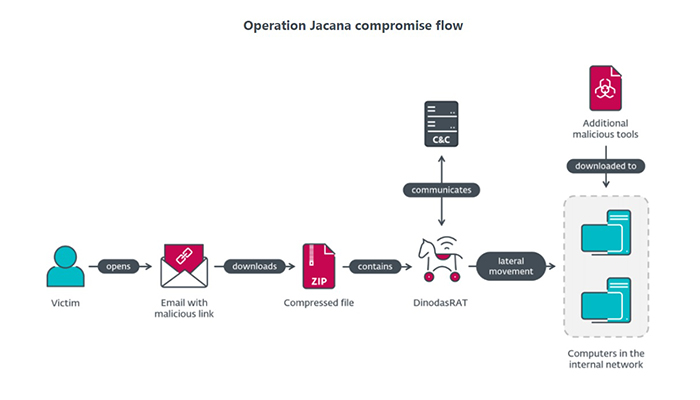
ESET researchers have discovered a cyberespionage campaign against a governmental entity in Guyana. Named Operation Jacana by ESET, they believe with medium confidence that it is linked to a China-aligned threat group. In the attack, the operators used a previously undocumented backdoor, DinodasRAT (Remote Access Trojan), that can exfiltrate files, manipulate Windows registry keys, and execute commands, and it encrypts the information it sends to the command and control server (C&C) using the Tiny Encryption Algorithm.
This campaign was targeted, as the threat actors crafted their emails specifically to entice their chosen victim organization. After successfully compromising an initial but limited set of machines with DinodasRAT, the operators proceeded to move inside and breach the target’s internal network, where they again deployed this backdoor. It has various capabilities that allow an attacker to spy on and collect sensitive information from a victim’s computer. Other malicious tools, such as a variant of Korplug (aka PlugX), were also deployed.
Korplug is common to China-aligned groups, for example, Mustang Panda. The attribution to a China-aligned threat actor is made with only medium confidence. This attribution is further supported by recent developments in Guyana–China diplomatic relations. In February 2023, the same month that Operation Jacana took place, the Special Organized Crime Unit of Guyana arrested three people in a money-laundering investigation involving Chinese companies, an act disputed by the local Chinese embassy.
“This domain indicates a Vietnamese governmental website; thus, we believe that the operators were able to compromise a Vietnamese governmental entity and use its infrastructure to host malware samples. ESET researchers notified the VNCERT about the compromised infrastructure,” said Fernando Tavella, ESET Researcher who discovered Operation Jacana.
The deployed spearphishing emails referenced recent Guyanese public and political affairs, indicating that the attackers are keeping track of their victims’ (geo)political activities to increase the likelihood of the operation’s success. One email, luring the victims with news concerning a “Guyanese fugitive in Vietnam,” contained a domain ending with gov.vn.